Internet Of Objects
All You need is just to clic over a title or subtitle in order to display its content - Imad Taje Eddine

The Internet of Things occupies increasingly growing place in the digital univers .An Internet of Things that goes beyond communication Machine To Machine, beyond sensor networks, beyond the simple dimension technological or labeling objects and that puts people at the center. Internet of objects carried by a transformative vision that changes and strengthens the relationship between objects and humans and extending our tools, our senses and our consciousness through these objects networks.
The Internet of Things is one of the telecommunications sectors that should see the strongest growth in the coming years. Some estimates suggest 50 billion connected objects on the horizon 2020s But the term Internet of things is somewhat ambiguous. If the Internet is a technology that is proven, it is not fully adapted to the capillary networks connecting objects. An adaptation effort is necessary to take into account the very large number of objects to manage, which often have high energy demands and limited processing capabilities. We Must also incorporate the fact that the information which give access these objects are sometimes intrusive by nature so any action can have critical consequences.
Nevertheless the term Internet of Things, reflects the idea to trace the real world information (or to transmit instructions) towards computer systems using the most generic possible technologies and offering greater interoperability to implement innovative services. It is opposed to proprietary and closed approaches, although they should be, in any way, considered because of the lifetime of an object which can be more than ten years, while the protocols used in networks can follow a shorter development cycle.
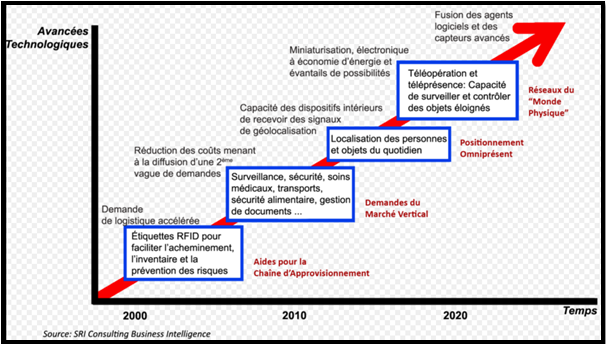
networks are potentially affected by the Internet of Things. It combines applications related to automation, the remote reading of meters or more generally to smart grids that integrate a computer control plane to electrical distribution systems, industrial networks to replace proprietary protocols or intelligent transportation, clothing smart ... ... the Internet of things can also be seen as a democratization of network usage by a drastic reduction in communication costs. Even if some concepts are in minds for years (as the connected beverage dispenser, the statement of remote meters, or home automation, etc.), the cost of communications equipment and associated transmissions annihilate all the hope of a possible commercial success of these solutions.
The main current Internet force, that can be called Internet of contents, is to offer a coherent and open ecosystem, facilitating the interconnection of equipment and promoting the creation and deployment of new services.
To sum up, we can say that this is a new revolution begins to take place in everyday life of the human being. Everything becomes faster and more accurate and above accessed anywhere and anytime. Soon the world will see a new era with an interesting domination of connected objects for convenience and above all more performance in everything we do. Wait patiently until day. In the life of a company, it will not be possible to dispense with the IoT. Yet, because of ignorance or poor learning of the Internet of Things, employees sometimes use old technology. It is a source of productivity loss, sometimes very important and unrecognized large companies.
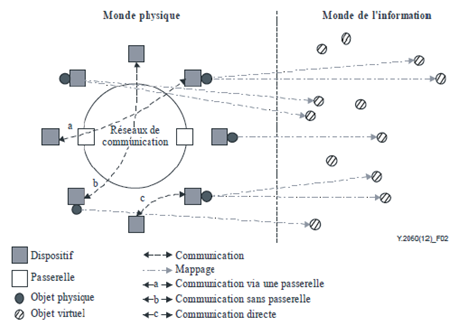
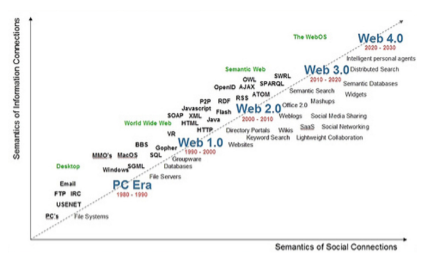
Discussing the interconnection of objects requires a focus on two central definitions: Web of Things and the Internet of Things. Web of Things refers to the extension of the World Wide Web (the Internet network as we know it today) to objects that are not generally connected. These devices connected to the Internet in order to maximize their abilities. The Internet of Things is more a new type of network, a web that involve objects connected in a Web 3.0.To make it simple,the objects are connected to each other and could exchange information without going through a third party.
It's probably not necessary to remember that the Internet of Things was the dream of its pioneers, but we are far away. Indeed, interactive objects are now almost nonexistent. Far talkative objects we waited, we find ourselves surrounded by objects connected to the same network but are blind to each other. In the best case, only to whom these devices communicate are firms that have put the world. It is closer to Web 1.0 Web 3.0 that supposed to embody the future.
Nevertheless, hope remains. It is possible that the Internet of Things is still in its first phase of existence: we seek,innovate,still testing on our side. Several infrastructures are currently being put in place to erase those boundaries. Examples include the Lab of Things, the new operating system developed by Microsoft. Specially designed for the Internet of Things, it offers a dashboard for managing different devices connected to the home, to centralize all these multiple connections. Sure, the principle remains the same: the objects talk to each other indirectly, again via a home server, but the will is there. A desire to gather all the devices connected to a home in a single network. It hard to do better when objects can not understand them.
This is a question that comes naturally when one examines the interconnection of objects. Indeed, if it is desired that two different devices can operate each other, we must think about a system where objects use the same communication protocols. This raises the question of standards. In general, everyone agrees to find the positive principle. Internet itself owes its success to the universal adoption of certain communication protocols (HTTP including the famous, that you find in front of each web page). This is a common language, no matter the computer, the operating system or browser, enables Internet to be used by everyone in the same way. We can even move us to say that it is thanks to these standardized protocols that the Web has become this mass of information that we know today.
Therefore, what the major brands of the Internet of Things are waiting for to define such standards? In this case, the problem is not lack of them but their overabundance. Occupied to fight to impose their own communication protocols, most large firms do not allow objects connected to form the largest network that everyone expects. The problem , however,it has been clearly identified since a practical solutions has began to manifest as (IPv6 over Low power Wireless Personal Area Networks), which connects the objects directly on the cloud rather than through a third device (smartphone , Tablet). Unfortunately, although it is probably a pioneer in the Internet of Things, it will become a standard only if it is used by the wholes connected devices. Stay tuned.
It is impossible to address the challenges of the Internet of Things without mentioning safety. If the question also arises as to the traditional Internet, it is even more vital when it comes to computers but not personal items, cameras or other connected device. The subject is particularly sensitive since the articles about Shodan (search engine able to detect any connected object in the world, which we mentioned previously here) or pirated refrigerators without any protection (little reminder here) . The traditional Internet acquires antivirus, antimalware and increasingly effective firewalls to counter this problem, so that a real market has developed around these software. If the subject of Internet wants to turn off, it will be primarily to alleviate these security concerns finally developing appropriate protection and regularly updated for our connected devices.
Creating an ideal Internet of objects is useless if it remains confined to a marginal use. Admit it , despite the extremely interesting products that exist on the market today, few people in France at least, Have connected objects. By "people," we mean of course of "individuals", with a medium budget and lifestyle of you and me. Raison: sometimes abnormally high prices and scarcity of physical outlets (LICK is a chain of stores connected objects), eliminating any chance of spontaneous purchase. Low supply which is consistent with a minimum request. It must be said that for now, the Internet of Things is not anchored in mentalities. The lack of information on the subject that few people know the appreciation of certain devices (when they do not completely ignore the existence of connected objects). Often the use of these products can be considered superfluous and for a marginal public, while many objects are connected to help the health, welfare or comfort and might interest everyone. Clearly, if it is desired that the Internet of Things really takes off, it will be informed about this and to make these products available to the greatest number.
If we go beyond the issue of single performance of a system, we must distinguish three classes of problems: first, the flexibility (implementation solution can evolve with the context), second interoperability (setting solution work can communicate with other solutions), third safety (the solution is secure for both the data but also for people who use it).
It is useless to acquire an expensive solution that will change in a few months. In a supply chain context, it is essential that the whole system can evolve and adapt. It is unthinkable to have such a solution that works in good weather but not when it is raining (humidity affects indeed RFID solutions for performance). Similarly, if the procedures are going, we must make the system flexible enough to incorporate new rules without jeopardizing the entire system both in hardware and software. Similarly, if the company decides to change ERP or to develop it, does it imply the change of middleware or any or part of the RFID solution? This case nevertheless illustrates some theoretical issue related to the scalability of RFID solutions.
Nearly 140 organizations worldwide are now involved directly or indirectly, by the standardization of M2M communication. This standardization phase represents indeed one of the crucial factors in the evolution of the mobile Internet into the Internet of Things.
There are thousands of "specific" standards to specific contexts of the IoT, such as RFIDs, radio standards, special applications to a domain (for example, the health sector, the auto ... .. ). It would be very difficult to go through all these steps, we can do against a particular focus on initiatives concerning the standard "generic" of the IoT, especially those already used by 'industry.
First, we analyze the initiative known as the most universal, the IOT-GSI: Internet of Things Global Standard Initiative supported by the international body the ITU (International Telecommunication Union).
 We will focus on two recommendations ITU-T Y.2060, which provides an overview of the concept of
IOT and ITU-T Y.2060, which describes the conditions for the machine interface oriented
communications applications in 'NGN (new generation network).
We will focus on two recommendations ITU-T Y.2060, which provides an overview of the concept of
IOT and ITU-T Y.2060, which describes the conditions for the machine interface oriented
communications applications in 'NGN (new generation network).
Recommendation ITU-T Y.2060 provides an overview of the Internet of Things (IoT). It explains the concept and scope of IoT, which defines the basic characteristics and the high-level requirements and describes the reference model. The ecosystem of the IoT and different business models are also presented in an appendix given for information.
 A technical overview of the IoT:
A technical overview of the IoT:
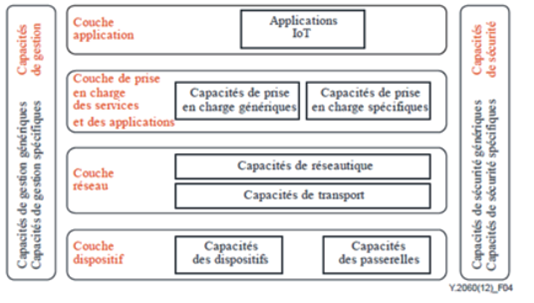
The reference model in four layers of the IoT:
 Recommendation ITU-T Y.2061 provides an overview of machines oriented communications
applications (OMC) in the environment of next generation networks (NGN). In particular, it describes
a JI ecosystem characteristics OMC communications and some use cases. From an analysis of
applications of JI Service Requirements, specifies the network capability requirements and NGN
requirements for capacities in the field of MOC devices.
Recommendation ITU-T Y.2061 provides an overview of machines oriented communications
applications (OMC) in the environment of next generation networks (NGN). In particular, it describes
a JI ecosystem characteristics OMC communications and some use cases. From an analysis of
applications of JI Service Requirements, specifies the network capability requirements and NGN
requirements for capacities in the field of MOC devices.

We will see in a second step a focus on network part and in particular on standardization parallel efforts by the IEEE and IETF in the field of sensor networks over IP. These efforts have initially realized by the proposal of a model of layers of the OSI model and more appropriate protocols for industrial networks that TCP / IP over Ethernet model.
Ces efforts se sont d’abord concrétisés par la proposition d’un modèle de couches sur le modèle OSI ainsi que de protocoles plus adaptés aux réseaux industriels que le modèle TCP/IP sur Ethernet.
The standards of the ETA and the IETF about the Internet of Things mainly concern network protocols in general
The IEE’s initiative was about to expand the classical model layer TCP / IP, by introducing more appropriate protocols to the IoT at different layers. Nevertheless exchanges between connected objects can both use the classic standards of the Internet, that is to say, Ethernet, IP, TCP / IP, HTTP.
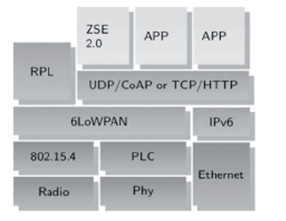 We will briefly describe some of those protocols which appear at different layers of the model below.
We will briefly describe some of those protocols which appear at different layers of the model below.
The PAN (Personal Area Network) group equipment is controlled by a single user over short distances (about ten meters).
The 802.15 standard defines the IEEE Wireless PAN called WPAN (Wireless PAN) whose technologies are Bluetooth, IEEE 802.15.3 (WPAN broadband) and IEEE 802.15.4 (WPAN low flow or Low Rate).
The 802.15.4 is about communication protocols for wireless networks of the family WPAN LR (Low Rate Wireless Personal Area Network) due to their low consumption, low-range and low-flow devices using this protocol.
It allows to provide energy autonomy of several months or years. The 802.15.4 is used by many implementations based on proprietary protocols such as ZigBee or 6LoWPAN IP like.
IPv4 and IPv6 are effective for delivery of data for local area networks, metropolitan area networks and wide area networks such as the Internet. However, they are difficult to implement in network sensors and other systems constrained in particular because of the large size of headers. 6LoWPAN, actually stands for "IPv6 Low Power Wireless Personal Area Network", was designed to allow IPv6 to integrate these forced hardware and networks that interconnect.
The "EPC Global Standard" initiative of the Global Standard1, which is a non-profit organization for developing standards with members in over 100 countries. We discuss the EPC (Electronic Product Code) as a unique individual identifier for identifying an electronic product as well as the EPC global Network architecture that defines the organization of information systems designed to ensure the exchange of EPC data globally. One of its main components, the ONS (Object Naming Service) is directly based on the DNS (Domain Name System).
In the middle of the great distribution, a standard has emerged since the 1970s for product identification: the EAN (European Article Numbering). This is the barcode found today on the vast majority of consumer products.
 EAN code is not used to identify a class of products, or individual instances of this class. However,
such a distinction at the individual level is essential for the emergence of the Internet of Things, as
well as assigning a unique IP address to each connection and this is mandatory for operation of the
Internet as we know it today. This is the EPC (Electronic Product Code) developed by the Auto-ID
Center at the Massachusetts Institute of Technology (MIT) which asserts as new standard.
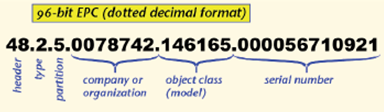
An example of encoding EPC:
EAN code is not used to identify a class of products, or individual instances of this class. However,
such a distinction at the individual level is essential for the emergence of the Internet of Things, as
well as assigning a unique IP address to each connection and this is mandatory for operation of the
Internet as we know it today. This is the EPC (Electronic Product Code) developed by the Auto-ID
Center at the Massachusetts Institute of Technology (MIT) which asserts as new standard.
An example of encoding EPC:
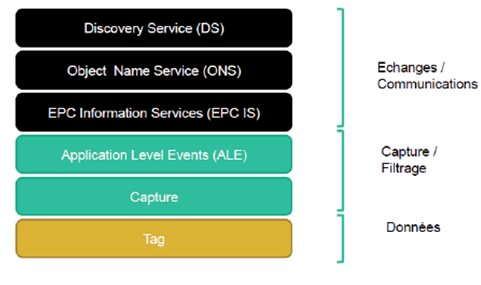 In addition to this, we have EPCglobal Network architecture, which defines the organization of
information systems designed to ensure the exchange of EPC data globally.
In addition to this, we have EPCglobal Network architecture, which defines the organization of
information systems designed to ensure the exchange of EPC data globally.
Finally, we will focus on the initiative of OASIS (Organization for the Advancement of Structured Information Standards) is a nonprofit consortium that guides the development and adoption of standards "open" to the Society information.
The work of the consortium on the Internet of things concern the standard network and messaging technologies such as Message Queue Telemetry Transport (MQTT) Advanced Message Queuing Protocol (AMQP) as well as the data distribution service (DDS).
Les travaux de ce consortium sur l’internet des objets portent sur les technologies de réseau et de messagerie normalisées comme Message Queue Telemetry Transport ( MQTT), Advanced Message Queuing Protocol (AMQP), ainsi que le service de diffusion de données (DDS).

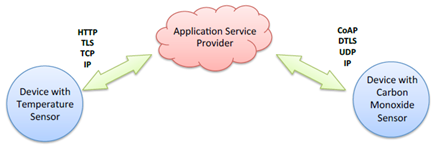
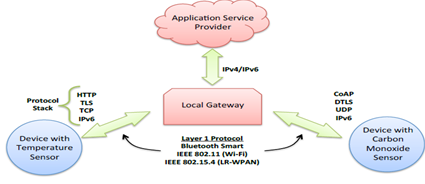
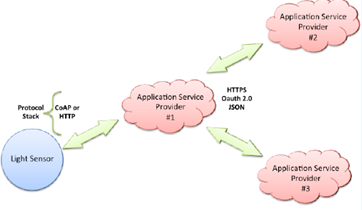
The massive arrival of connected objects in the everyday citizen , the interdependence of systems, data and associated processes facilitate the emergence of new value-added uses but also open many loopholes of security. There are ways to protect themselves by paying particular attention, firstly, to the components used for the design of electronic cards and secondly for the quality of software design. Most security problems are due to the existence of software vulnerabilities that can be architecture, design, implementation or configuration and are then exploited by attackers.
A major challenge lies in the ability to design architectures for which sensitive parts attacks have been identified and isolated, and to approach the maximum of no fault to the specification and implementation of this sensitive part.
In 2015, a European has averaged 7 connected objects. Although US startups are forerunners in this field, France is not left with a vigorous policy for growth of the sector and companies active as Withings, Netatmo or Smokio.
Still, for the moment, 49% of French believe the objects connected too expensive. Companies will therefore have to reconcile the classic strategies of selling products with complementary services related to the use of collected data in order to maintain a new relationship with their customers and improve the quality of their products and services. Companies must also start now to think about new strategies around connected objects.
Toco Toucan’s study highlights four types of business strategies incorporating connected objects:
The creation of a new brand experience with the renewal of its existing product lines by connecting them to the internet (Babolat, Seb, Oral B, BMW, etc.), The creation of new consumer experience in store / retail for loyalty customers and have better visibility on their purchasing behavior (Amazon, Kiabi, etc.), communication initiatives that highlight a young brand, innovative and willing to try the bet of connected objects during a campaign (Nivea, Oreo, Huggies, etc.), process optimization and internal monitoring, often with the use of a startup B2B (including eProvenance or Local Motion)
In 2015 the turnover generated by the connected objects related activities is expected to exceed EUR 400 million and, in 2020, we have more than 80 billion connected objects. The connected home is therefore a more Arles and the data collected now possible to consider a myriad of new applications. So there is a whole market to conquer.
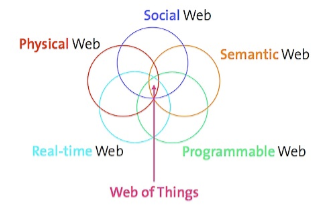
The Internet of Things is a born field of integration of physical objects (electronic systems with sensors and effectors) to the Internet. Web objects refers to the application running on this infrastructure, related Web technologies and standards. A physical object is seen as a set of services accessible through the web and the physical environment which allows you to specify the context.
The reuse of web standards allows especially to build interoperable, portable and open. Applications "web of objects" should allow:
Users interact with services, - services interact with each other and consist to form value-added services - users interact with these composite services.
These applications have many scientific and technological challenges. Moreover, it’s up to them to find their place in today's digital transformation of our society, and locks in terms of use and acceptability are to be lifted. Although the central perspective is that of the Web, a place of increasing importance is made to the Artificial Intelligence (AI). Web objects are themes in areas such as networks, embedded systems, the web, but also regarding software engineering and the use of digital worlds. It is also found in the combination of multiple domains providing representations, treatment and automated reasoning: web data, multi-agent systems, decision support, learning, planning, etc.
Web objects refers to the integration of any searchable or remotely controllable appliance, in the world of World Wide Web.
Networking of smart objects on a large scale from the real world (for example with RFID chips, part of wireless sensor networks, or embedded systems) became the goal of many recent research activities and varied. Although more than a representation of data and functionality by the concepts of vertical systems, smart objects are part of the web.
In the Web objects, the popular Web technologies (HTML, JavaScript, AJAX, ...) can be used to develop applications that use smart objects. Users can use the well-known Web mechanisms (navigation, search, labeling, caching, connections) to interact with them.
Multiple prototypes use these principles in a sensor environment, energy monitoring systems and RFID objects on the Web. ad-hoc applications such as Applications Composites Physical emerging more and more by the ease of development and integration (small size).
The HTTP protocol is used in Web objects as application protocol: HTTP provided by operations (GET, POST, PUT, DELETE) to provide resources of an object connected the four basic CRUD functionality control, then define them in a uniform interface with a known and shared semantics.
TOn the Web, the identification of a resource is made by a URI representation. A smart object can have many resources (sensors, actuators, energy source, radio interface, ...), each of which can be linked to one or more other resources structured hierarchically, these resources also provide back links to the resource-parent or transfer to the child resources. Modeling this object (URI resources, their links, their hierarchies) is not strictly necessary in itself, but good design of these URI will facilitate the work of developers on the discovery and understanding of different resources and their interactions.
Applications using intelligent objects may need to be subscribed to different information about the object or set of objects they use. With Atom, the Web has a standardized model and RESTful to interact with information gatherers; the Atom Publishing Protocol protocol also adds interactions in read / write mode. Any information or operation of an object or set of objects can thus be stored in a buffer memory, allowing users to monitor these objects by subscription Atom feed on a remote server rather than unitary interrogate all objects.
The central idea of REST is focused on the concept of resource as one of the components of an application to be used or considered. A resource can represent a physical object (eg a temperature sensor), but also an abstract concept such as collections of objects.
REST offers two basic rules: identifying a resource using a URI, and the definition of a uniform interface by using the HTTP protocol. Another priority of REST is the simple point-to-point communication via HTTP using formats such as JSON or XML.
Web objects defines the opening of the web objects: accessibility and interoperability are major aspect in choosing and designing an architecture. Communication between applications resident on an object and web applications is called Web Service.
In the future, all the objects around us will be connected, we can even speak of connected plants. The sensor for green plants wifi monitors the health of your plants indoors and outdoors. The data is sent to an online server and the user can access them anywhere, anytime with a smartphone or computer. You know, even when traveling far away, the health of your plants. If they suffer, a message is sent to your mobile.
How many times have you seen an object in a catalog that you want to buy but you do not know how it would fit your environment? This application of augmented reality can help in this case. You can virtually severing the object and transform its image in 3D at home or in your office. You can also test paintings on your walls and architects can see in advance what will look like a building in its environment when finished.
We used to say: "I'll leave you the keys under the mat." From now on, you can lock and
unlock your door from anywhere in the world. Any smartphone can use a technology called
Lockitron. This is a keyless lock that you can install on your door. For example, you can open a
remote friend via a smartphone, without having to give him the keys. You are also alerted if someone
tries to open the door.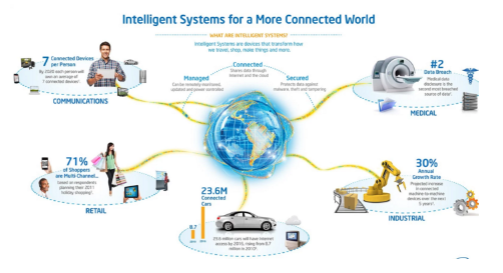
To conclude , it seems to me that to address the "Internet of Things", we can retain a French literature review four formulas: Internet of Things, Objects Connected, Connected Information Systems Delivered to Objects and Services Connected via objects.
Reading this list shows that the "Internet of Things" is still floating field and it would be rash to stop a final speech, including security. However, in order to move towards this speech, this list of four formulas may suggest companies four views, which are respectively legal, technical, operational and commercial.
The first view, which governs the other, is the legal point of view. The use of connected objects reveals significant risks especially in terms of protection of privacy and accountability to users and manufacturers. For the latter, the legal corpus reveals a set of obligations that companies must meet especially in the applicable standards and norms to the airwaves. The combination of these elements requires players to act as upstream at a critical practice of CSR, but also in terms of the design of connected objects or an approach of "Privacy by Design" is widely encouraged.
The technical side opens the potential field. In line with the heritage of the Internet, the technique focuses on interoperability standards. These standards put forward an overall architecture of a system with connected devices, network protocols used by the objects, an addressing objects and messaging mechanisms between objects. Security is immediately processed in each standard.
Operationally speaking, For large companies, the introduction of connected devices and their connection to the information system introduced major changes: the nature and volume of data, perimeter of the corporate network, access location and users and even physical hardware impacts on people stack of old and new technologies ... These contextual changes require an adaptation of the security approach at the project level, adapting and strengthening existing tools and methods and expanding governance.
Companies will also anticipate changes in internal operations related to the introduction of connected objects and to ensure the confidentiality, availability and integrity of information systems, and securely manage its opening.
Finally, the commercial point of view the actual address via use. The company must expect the unexpected uses, misappropriated, sometimes inconsistent or even malicious or illegal. Furthermore, due to the boarding sensors and actuators, the use of a connected object raises risks to people, property and the environment. The governance of information systems connected to the objects can be arranged by instituting a charge of use alongside the Project Manager Project management and Project Manager Project management, customer experience phase in a real situation, a specific work of defining the terms of use and funding of specific features ensure consistent use. We can expect an evolution of collective representations of the information system function.